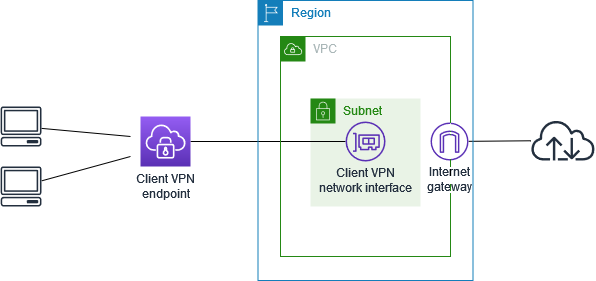
Amazon Web Services (AWS) offers a VPN Client that is particularly advantageous for organizations seeking scalable and secure connectivity solutions compared to traditional VPN services like NordVPN. This distinction is largely due to the inherent flexibility and elasticity of cloud-based services provided by AWS, tailored to meet the dynamic requirements of modern businesses.

The examination of GitHub Actions involves a comprehensive evaluation of its functionalities, features, and overall effectiveness. GitHub Actions is a powerful tool for automating workflows within the GitHub platform, enabling seamless integration and continuous delivery processes. It facilitates the automation of tasks such as code compilation, testing, and deployment, contributing to an efficient and streamlined development pipeline.
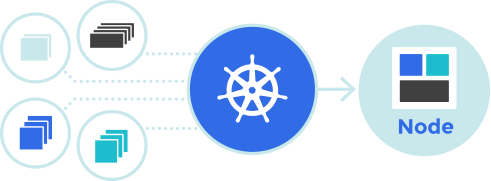
This shows the steps required to configure the control and data plane of a Kubernetes deployment on AWS using EKS and the autoscaling service.

It based on cards, there are four different card types depending of the functionality.

This tool provides static code analysis into your Cloudformation templates, enforcing these checks in your code will allow infrastructure developers to create better templates.
